sPACE Attack: Spoofing eID’s Password Authenticated Connection Establishment
A Critical Man-in-the-Middle Vulnerability in the German eID Scheme

The objective of this article is to highlight a vulnerability within the eID scheme (“Online-Ausweis-Funktion”) of the German National Identity Card. This vulnerability compromises the hardware security, enabling an attacker to effectively carry out scalable Man-In-The-Middle attacks. The attack does not require remote code execution, physical access, or similar approaches and can be executed through apps uploaded to the official app stores. Such attacks compromise access to services that rely on eID security, including government services, eHealth platforms, and banking systems. Additionally, the attacker can extract the personal data stored in the eID. This attack requires no special privileges and can be executed remotely. Due to the nature of the vulnerability as a design flaw, implementing countermeasures may prove challenging or impractical.
The vulnerability has the CVE-ID CVE-2024–23674 and a CVSS rating of 9.7 (Critical). The full research paper is available for download at the end of this article.
A responsible disclosure process was conducted with the BSI (Bundesamt für Sicherheit in der Informationstechnik), during which the BSI acknowledged the presence of the vulnerability. Their defense centers on the user’s responsibility for maintaining the security of their client devices. However, users typically exhibit poor security practices. In addition, this paper demonstrates that the attack remains successful even when all BSI recommendations are followed and client devices are updated.
BSI: “Yes, we agree that your described scenario enables an attacker to authenticate against a relying party using the eID of a victim through compromising the user space.”
Background
The German eID scheme, commonly referred to as the “Online-Ausweis-Funktion,” is a digital identity system provided by the German government. Integrated as a component of the German National Identity Card, this functionality enables secure and user-friendly online authentication processes, as well as the generation of digital signatures for citizens. The system is designed to be versatile and secure, allowing users to access various online services, including government portals, tax filing, health services, insurances, banking, and e-commerce platforms.
At the heart of the German eID scheme is a state-of-the-art chip designed according to the highest standards of hardware security. This secure element, integrated directly into the identity card, serves as the hardware factor for digital identity and cryptographic operations. The chip is equipped with security features that provide resilience against a spectrum of potential threats. The chip facilitates secure communication through the implementation of standardized protocols (“General Authentication Protocol”), using the Application Protocol Data Unit (APDU) format for secure data exchange between the card and the eID server.

The Rise of the Basic Readers
The German eID system specifies different levels of readers, as outlined in BSI TR-03119:
- Basic Reader (Cat-B): Basic Readers (Cat-B) are suitable for home use and are typically integrated devices like smartphones or notebooks. Unlike other categories, the basic reader does not necessitate a “PIN pad (secure PIN entry) with PACE support.” It is commonly utilized in low-security scenarios such as “age verification,” “eTicketing,” and “Internet shopping” (refer to BSI TR-03119).
- Standard Reader (Cat-S): Standard Readers (Cat-S) are physical smart card readers equipped with a PIN pad to ensure secure PIN entry. Designed as the “eID function on the Internet with increased security requirements” this category enhances security for various online interactions.
- Comfort Reader (Cat-K): The Comfort Reader is equipped with a PIN pad for secure PIN input and a display featuring 2 x 16 alpha-numeric characters. This category supports all functions of the eID card, including the qualified electronic signature.
The original design choice of the eID scheme appears robust in terms of security, suggesting the use of basic readers for low-security situations and standard or comfort readers for scenarios demanding substantial or high security. However, the challenge arises due to the lack of market adoption for physical readers. In practice, most German citizens rely on their smartphones to interact with the eID card, either directly when using the eID on the smartphone or as a reader for the AusweisApp on a laptop. Therefore, in practical terms, only basic readers are left today.
The Vulnerability
The design flaw in the German eID scheme manifests in two aspects:
- The insufficient decoupling of the two authentication factors (physical possession and knowledge/PIN), enabling an attacker to compromise both factors simultaneously, and
- the absence of mechanisms validating the endpoints between the eID server and the user’s eID client, thereby leaving room for Man-in-the-Middle (MITM) attacks through spoofing.

The attack involves placing a modified eID-Kernel on Alice’s device, redirecting both the APDUs and the PIN. Importantly, executing this operation does not require any special permissions on Alice’s device, allowing for the manipulation of the Password Authenticated Connection Establishment (PACE) protocol in the eID, thereby coining the term “sPACE Attack” (Spoofing Password Authenticated Connection Establishment).
Why does the attack work? The German eID scheme lacks a secure PIN entry mechanism for basic readers, as highlighted above. Considering that the physical chip is in proximity to the device where the PIN is entered, Mallory can exploit both the hardware factor (using APDU redirection) and the knowledge factor (by intercepting the PIN entry) in a single attack. Additionally, the eID system inadequately verifies the identity of the actors at both ends of the encrypted channel, allowing an attacker to impersonate Alice. Notably, the eID system lacks true end-to-end encryption, as the PIN entry occurs on an unsecured endpoint.
By deploying an update to an existing app or persuading Alice to install a malicious app from the app store, this attack can be carried out without requiring any specific permissions on Alice’s device. This remains effective even if the user adheres to all of the BSI’s security recommendations.
A detailed description of the vulnerability, a proof of concept and potential countermeasures can be read in the research paper available at the link at the end of this article.
Proof of Fraudulent Bank Account Opening
To demonstrate the practical exploitability of the vulnerability, a bank account has been successfully opened in the name of a victim at a major German bank. As a result, the attacker has access to the newly established bank account owned by the victim. It is important to note that the victim used a smartphone updated to the latest version with all patches installed and followed all security recommendations provided by the BSI. No physical access or remote code execution was required.
Note: The author implemented precautions to ensure that no other users were impacted by the exploit. However, it is important to understand that this exploit had the potential to affect every user with the app installed if the author had chosen to do so. Furthermore, the victim agreed in advance to the attack, to avoid legal issues.
The victim is a German citizen who owns an iPhone and a German ID card equipped with activated eID functionality. The victim intends to use the eID to access the official portal of the Arbeitsagentur (refer to https://www.arbeitsagentur.de/). To do so, the victim visited the official Apple app store and downloaded the official AusweisApp.
The victim opened https://www.arbeitsagentur.de/ on the smartphone and initiated the login process for the Arbeitsagentur.
Note: The service the victim attempts to access is not important. Any service that initiates the link to the AusweisApp would have triggered the attack. As demonstrated in the research paper, phishing attacks are also effective.
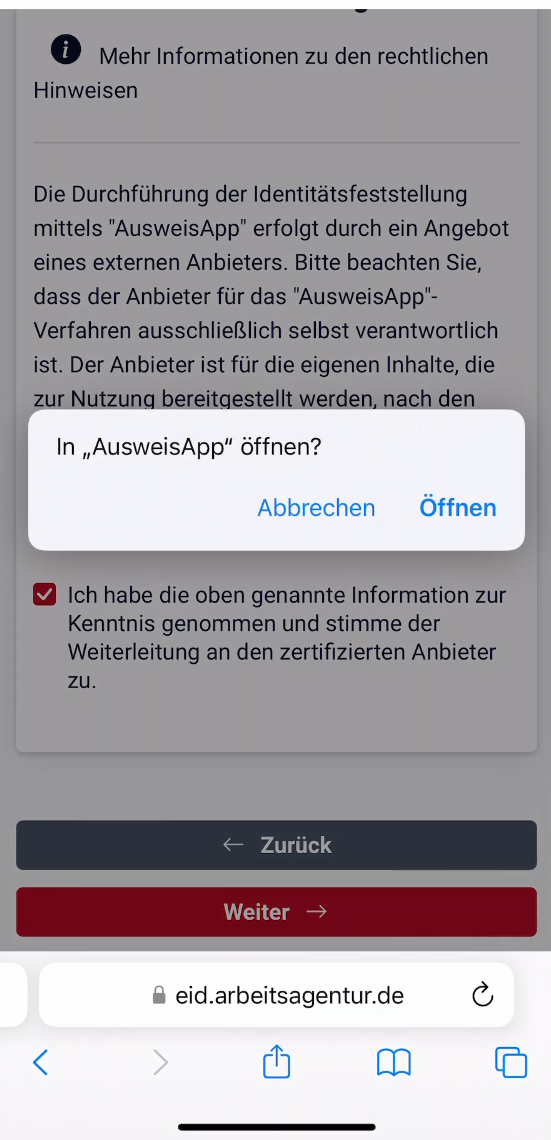
At a certain point of the login process, there is a redirection (“deeplink”) to the AusweisApp, where the eID authentication is intended to take place. As show in the research paper, both Apple’s and Google’s deeplink behavior, combined with the approach the eID uses for deeplinks, can be utilized by an attacker to redirect to another app.
As a result of this deeplink vulnerability in the eID, an app containing a modified eID kernel, uploaded to the official app store by the attacker, was triggered. Importantly, this does not require any permissions, no remote code execution or physical access.
The next screen shows the triggering of the “AusweisApp”. It is important to note that this is not the legitimate AusweisApp downloaded just a minute ago, but an app owned by the author, including a modified eID kernel.
The victim is now within the malicious app, performing an eID identification. This eID process takes a bit longer than normal. In the background, the modified eID kernel executed the attack, redirecting the APDUs and the PIN to the attacker.

Following the attack, the attacker allows the victim to complete the intended eID login for the Arbeitsagentur. The victim successfully accesses the Arbeitsagentur and remains unaware to the just executed attack.
On the attacker’s side, the attacker initiated the system to listen for incoming connections from victims. Upon the victim’s initiation of the modified eID kernel within the malicious app, a connection is established to the attacker’s system. The attacker system responds to this connection by initiating the bank account opening process at the bank.
Note: The name of the affected bank will not be disclosed, as the specific bank is not important. Any relying party using the eID system is vulnerable to this attack.

The attacker extracted data from the eID using the “Selbstauskunft” and utilized this information to complete and submit the account opening form at the bank.
The attacker’s system proceeded with the identification process for the bank account opening. This action once again activated the AusweisApp on the attacker’s system. The eID of the victim was accessed for a second time, enabling the identification for the bank account opening. Finally, the process finished, granting the attacker access to the newly created bank account associated with the victim.
The attacker now has access to a bank account which belongs to the victim.
Responsible Disclosure and BSI Response
After the discovery of the vulnerability, a responsible disclosure has been initiated with the BSI. A first version of this paper has been provided and a timeline of 45 days in line with the process defined by the BSI as detailed in the ‘BSI CVD guideline for security researchers’ has been set.
The BSI confirmed the vulnerability (“Yes, we agree that your described scenario enables an attacker to authenticate against a relying party using the eID of a victim through compromising the user space.”). However, their primary counterargument centers on placing the responsibility for client device security on the user, citing legal obligations for the citizen (“ensuring a secure operational environment at the client side is an obligation of the ID card owner per §27 (2) and (3) PAuswG.”). These obligations for citizens to ensure a secure operational environment include regular updates to the operating system, anti-virus programs, and firewalls (refer to the BMI advice).
1. The reply essentially confirms that the German eID provides only client-side security when basic readers are used. The security level is determined by the weakest link, which, in this context, is the user’s device. That other components of the system, such as the chip or the eID server, possess higher levels of security becomes irrelevant as an attacker will invariably target the weakest link in a system. For certain attack vectors, such as deeplinking and phishing, the security level can even be considered as falling below client-side security, as these vectors do not require compromising the user’s device.
2. Assigning responsibility for security solely to users is an irresponsible approach. It is a well-established fact that users often face challenges in maintaining robust security practices. Relying on everyday citizens to consistently stay updated with the latest patches and anti-virus software is likely impractical. Notably, the BSI’s security advice lacks guidance on phishing. Any security system, including the German eID, that places responsibility for security solely to users is fundamentally flawed in its design.
3. The claim that users can prevent such an attack by following security advice is not correct. The research paper outlines various potential attack vectors, including the deeplink vulnerability, phishing, remote exploits, and supply chain attacks. Of these, only the remote exploit is effectively addressed by the BSI’s security advice. Notably, the deeplink and phishing vectors are effective even if the operating system is updated, and antivirus programs and firewalls are in place. The proof of concept clearly demonstrated the effectiveness of the attack even on a fully updated system thereby proving the BSI’s answer as incorrect. Shifting the responsibility for security to everyday citizens is not only irresponsible but also ineffective in preventing the attack.
Given that the eID is employed to safeguard highly sensitive systems with the potential for substantial financial gains through attacks, it seems inevitable that this vulnerability will be exploited at scale.
Conclusion
The research paper has shown the existence of a vulnerability in the German eID scheme, posing a significant risk to all services relying on the eID, especially those handling sensitive data such as insurances, banks, and government services. While the BSI acknowledges the vulnerability, it places the responsibility on users for maintaining client device security. Contrary to this, the paper demonstrates that even with a perfectly secure client device, the attack remains effective.
The attack does not rely on remote code execution, physical access, or similar requirements. The only prerequisite is that the user has an app on their smartphone, which is uploaded to the app store by a malicious actor.
The available countermeasures have been discussed in the research paper, showing only limited viable options. Out of these, the author recommends:
- C6 / Client Side Security: Although acting as a temporary solution, this measure could enhance security to some extent.
- C9 / Deeplink Security: Implementing this countermeasure is highly recommended, as it would contribute significantly to security and there appears to be no compelling reason not to do so.
- C10 / Additional Authentication: Given that other countermeasures do not effectively address the vulnerability, combining the eID with additional authentication measures appears to be the most viable option to attain the required security level.
Unfortunately, beyond these recommendations, there seem to be limited alternatives to mitigate this vulnerability, outside of discontinuing the use of eID for substantial or high security use cases.
For communication, you can reach me at 0xCtrlAlt@proton.me or you can subscribe to updates by following my profile here on Medium. Please note that I may answer some of the question I receive in additional blog posts. My PGP fingerprint is 8A9D D1DF CA47 494C 35EF DC26 53B2 F3B1 88D6 E7D4.
This article, the logo, the images and the research paper can be used freely under CC BY 4.0.
The full research paper is available for download at https://www.dropbox.com/scl/fi/2powlii0dnmr7p7v5ijhc/2024_German_eID_02_Spoofing_PACE_final.pdf?rlkey=nx0ffmmbq3hffgxsuqwf0f45z&dl=0.
